Hello guys, today we are going to discuss about 5 most greatest scientists of India whose radiance became dimmer with time and the most shameful part is that we could not save their research books cause the british took them to their country and thus got the reward too. The best part comes when we realize that whatsoever had been searched by our greatest scientist is a part of our "Veda" and "Purana" which had been written much and much before birth of them. So imagine how great we Indians are and what kind of people they would be who had written the "Veda" and "Purana" by going beyond time in future being present in past. We are gonna dedicate this post as a small tribute to them.
1)
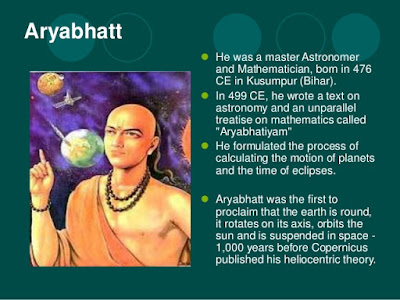
The Maharshi Aryabhata(महर्षि आर्यभट): We have entitled Aryabhat as "The Aryabhat" because no body can acquire the fraction part of the position which he had. While calculating the list of greatest scientists of ancient time, Aryabhat should must acquire the first place. The time when the whole world was busy in collecting food and water for their daily need, at that time Aryabhat the great had pointed out the truth of galaxy where the other countries were not even able to calculate 1,2,3. World knows that the exact relationship between earth and sun was pointed out by Nicolaus Copernicus but most of them don't know that Aryabhat had revealed it 1000 years before Copernicus. Aryabhat said that earth completes its revolution on its own axis around the sun along with the other planets of galaxy. He also told that earth as well as moon does not shine with their own light but they shine up due to light that comes from the sun. He also revealed almost correct circumference of the earth. Aryabhat also divided time along with earth's rotation. But the invention of
"zero (0)" had made him eternal forever. Zero without which considering mathematics would be futile as well as the whole digital world runs over binary number i.e, the combination of "0" and "1" had been revealed by Aryabhat. This invention along with other invention had made him eternal forever. Aryabhata wrote many mathematical and astronomical treatises. His chief
work was the ‘Ayrabhatiya’ which was a compilation of mathematics and
astronomy. Aryabhata also did a considerable amount of work in astronomy. He knew
that the earth is rotating on an axis around the sun and the moon
rotated around it. He also discovered the position of nine planets and
stated that these also revolved around the sun. He pointed out the
eclipses; both lunar and solar. Aryabhata stated the correct number of
days in a year that is 365. He was the first person to mention that the
earth was not flat but in fact a spherical shape. He also gave the
circumference and diameter of the earth and the radius of the orbits of 9
planets. He also came up with an approximation of pi (π) and area of a triangle.
He introduced the concept of sine in his work called ‘Ardha-jya’ which
is translated as ‘half-chord’.


2)
Maharshi Kanada(महर्षि कणाद): He is known as the father of Nuclear science. He had developed the theory of atom thousand years before the birth of John Dalton who had taken all the credits of invention of atom. He said that every matter of the world has made with atoms. He also revealed three laws of motion before the birth of Newton. Indian scientist and philosopher Kanada (Hindi : कणाद) had given Vaisheshika Sutra (in 600 BCE) which describes relation between forcce and motion etc which are as follow:
a)
वेगः निमित्तविशेषात कर्मणो जायते |
Means Change of motion is due to impressed force.
b)
वेगः निमित्तापेक्षात कर्मणो जायते नियतदिक क्रियाप्रबन्धहेतु |
Means Change of motion is proportional to the impressed force and is in the direction of the force.
c)
वेगः संयोगविशेषविरोधी |
Means: Action and reaction are equal and opposite.
3)
Maharshi Baudhayana( महर्षि बौधायन): It was ancient Indian's mathematicians who discovered Pythagoras theorem. This might come as a surprise to many, but it’s true that Pythagoras theorem was known much before Pythagoras and it was Indian who actually discovered it at least 1000 years before Pythagoras was born! Baudhāyana listed Pythagoras theorem in his book called Baudhāyana Śulbasûtra (800 BCE). Incidentally, Baudhāyana Śulbasûtra is also one of the oldest books on advanced Mathematics. The actual shloka (verse) in Baudhāyana Śulbasûtra that describes Pythagoras theorem is given below :
"दीर्घचतुरश्रस्याक्ष्णया रज्जु: पार्श्र्वमानी तिर्यग् मानी च यत् पृथग् भूते कुरूतस्तदुभयं करोति ॥"
Means: A rope stretched along the length of the diagonal produces an area which the vertical and horizontal sides make together.
Circling the square:
Another problem tackled by Baudhayana is that of finding a circle whose area is the
same as that of a square (the reverse of squaring the circle). His sutra i.58 gives this
construction:
“Draw half its diagonal about the centre towards the East-West line; then
describe a circle together with a third part of that which lies outside the square”.Square root of 2:
Baudhayana gives the length of the diagonal of a square in terms of its sides, which
is equivalent to a formula for the square root of 2. The measure is to be increased
by a third and by a fourth decreased by the 34th. That is its diagonal approximately.
That is 1.414216 which is correct to five decimals.
Other theorems include:
Diagonals of rectangle bisect each other, diagonals of rhombus bisect at right angles, area of a square formed by joining the middle points of a square is half of original, the midpoints of a rectangle joined forms a rhombus whose area is half the rectangle, etc.
4)
Maharshi Bhaskaracharya(महर्षि भास्कराचार्य): The first principle of gravity was stated by “Bhaskaracharya” and “not Newton”. Bhaskaracharya stated the laws of gravity in the book Surya Siddhanta in 11th century. Thus the law actually exists even before the birth of Sir Isaac Newton (Newton was born in the 16th century).
Here are some of the slokas from his book Surya Siddhanta that mentions how gravitation works :
"मरुच्लो भूरचला स्वभावतो यतो,विचित्रावतवस्तु शक्त्य:।।"
सिद्धांतशिरोमणि गोलाध्याय - भुवनकोश
आकृष्टिशक्तिश्च मही तया यत् खस्थं,गुरुस्वाभिमुखं स्वशक्तत्या।
आकृष्यते तत्पततीव भाति,समेसमन्तात् क्व पतत्वियं खे।।"
- सिद्धांतशिरोमणि गोलाध्याय - भुवनकोश
“madhye samantandasya bhugolo vyomni tisthati
bibhranah paramam saktim brahmano dharanatmikam”
[Surya Sidhantha 12th chapter 32 sloka]
This means: The spherical earth stands at the centre of earth in space due to the dharanatmikam sakti which prevents earth from falling away and helps it to stand firm.
“akrsta saktisca mahi taya yat svastham guru svabhimukham svasaktya
akrsyate tatpatativa bhati same samantat kva patatviyam khe”
[Sidhanta Shiromani, Bhuvanakosa, 6th sloka]
This means: Every object falls on the ground due to earth’s force of attraction. This force allows the sun, earth, moon and constellations to stay in the orbit.
5)
Maharshi Sushruta(महर्षि सुश्रुत): Maharshi Sushrut (600 BCE) :Father of Plastic Surgery
a genius who has been glowingly recognized in the annals of medical science. Born to sage Vishwamitra, Acharya Sushrut details the first ever surgery procedures in “Sushrut Samhita,” a unique encyclopedia of surgery. He is venerated as the father of plastic surgery and the science of anesthesia. When surgery was in its infancy in Europe, Sushrut was performing Rhinoplasty (restoration of a damaged nose) and other challenging operations. In the “Sushrut Samhita,” he prescribes treatment for twelve types of fractures and six types of dislocations. His details on human embryology are simply amazing.
Sushrut used 125 types of surgical instruments including scalpels, lancets, needles, cathers and rectal speculums; mostly designed from the jaws of animals and birds. He has also described a number of stitching methods; the use of horse’s hair as thread and fibers of bark.
In the “Sushrut Samhita,” he details 300 types of operations. The ancient Indians were the pioneers in amputation, caesarian and cranial surgeries. Acharya Sushrut was a giant in the arena of medical science.
Share this post to maximum people and let them all know about our eternal Indian scientist.
We are not saying that every invention has a root source of india but the beginning of scientific experiment was in india.
So, that's it for today guys. If you have any query then write it down to the comment section. We will be back very soon till then share this post because everyone should know about our marvelous indian scientists.




















































